logon
- Description: The factory is hiding things from all of its users. Can you login as Joe and find what they've been looking at?
- Difficulty: Easy
🔎 Solution
When attempting to log in with the username Joe, the application responds with: I'm sorry Joe's password is super secure. You're not getting in that way. This suggests that accessing Joe's account directly is not feasible.
However, logging in with any other arbitrary credentials results in the message: Success: You logged in! Not sure you'll be able to see the flag though.
Upon inspecting the browser's cookies, we notice three key values: username and password (both reflecting the input we provided), and admin=False.
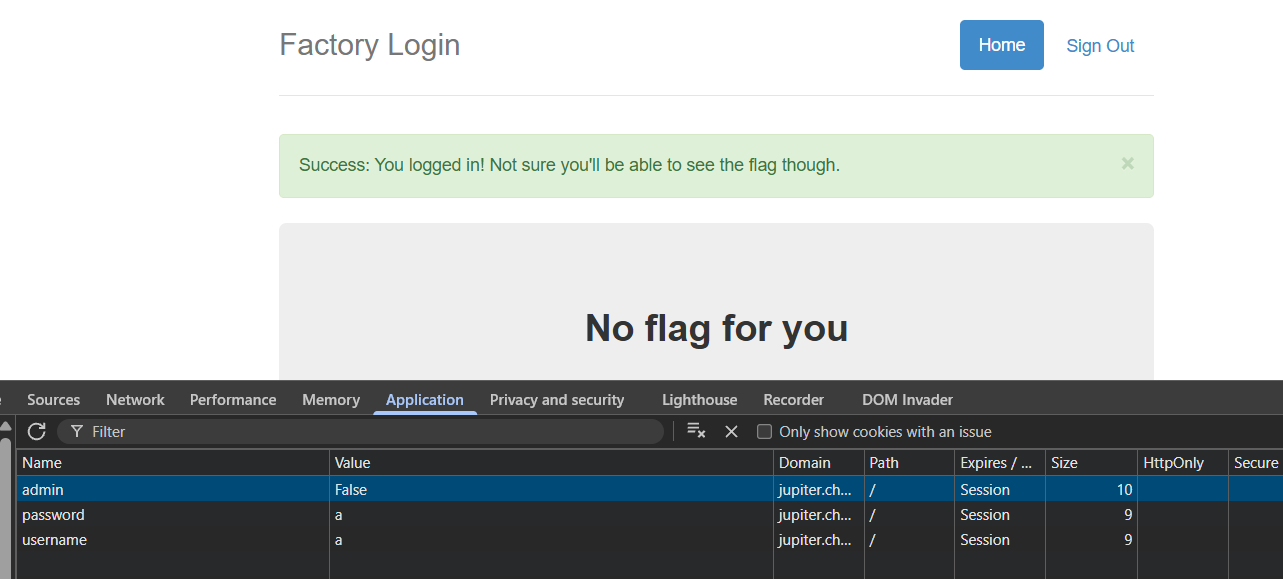
This indicates that the website uses cookies for access control - specifically, to determine whether a user is an administrator. This approach introduces a serious vulnerability known as Broken Access Control, which ranks among the top security risks in the OWASP Top 10. Broken Access Control occurs when applications fail to properly enforce restrictions on what authenticated users are allowed to do.
In this case, since the admin status is controlled entirely via a client-side cookie, simply modifying admin=False to admin=True grants elevated privileges.
After updating the cookie and refreshing the page, we are granted admin access - and with it, the flag.
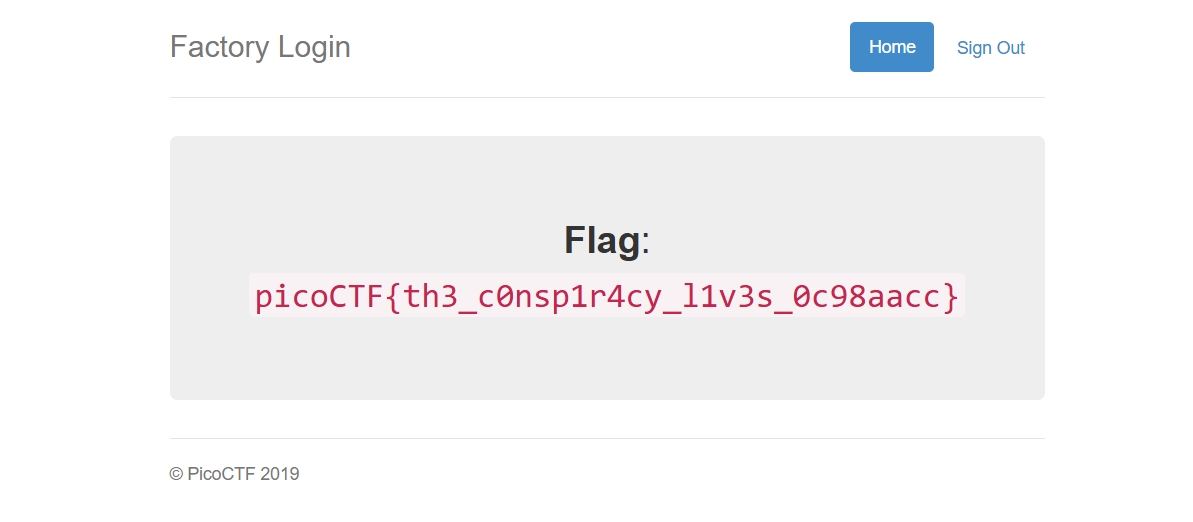
🚩Flag
picoCTF{th3_c0nsp1r4cy_l1v3s_0c98aacc}