head-dump
- Description: Welcome to the challenge! In this challenge, you will explore a web application and find an endpoint that exposes a file containing a hidden flag. The application is a simple blog website where you can read articles about various topics, including an article about API Documentation. Your goal is to explore the application and find the endpoint that generates files holding the server's memory, where a secret flag is hidden.
- Difficulty: Easy
🔎 Solution
The challenge website features a homepage displaying an article. Navigating to the #API Documentation section reveals details about the site's available endpoints.

Among them is a noteworthy endpoint: GET /heapdump, which, upon a successful 200 OK response, returns information about the site's memory allocation status.
Using the "Try it out" and "Execute" functions for this endpoint generates a .heapsnapshot file.
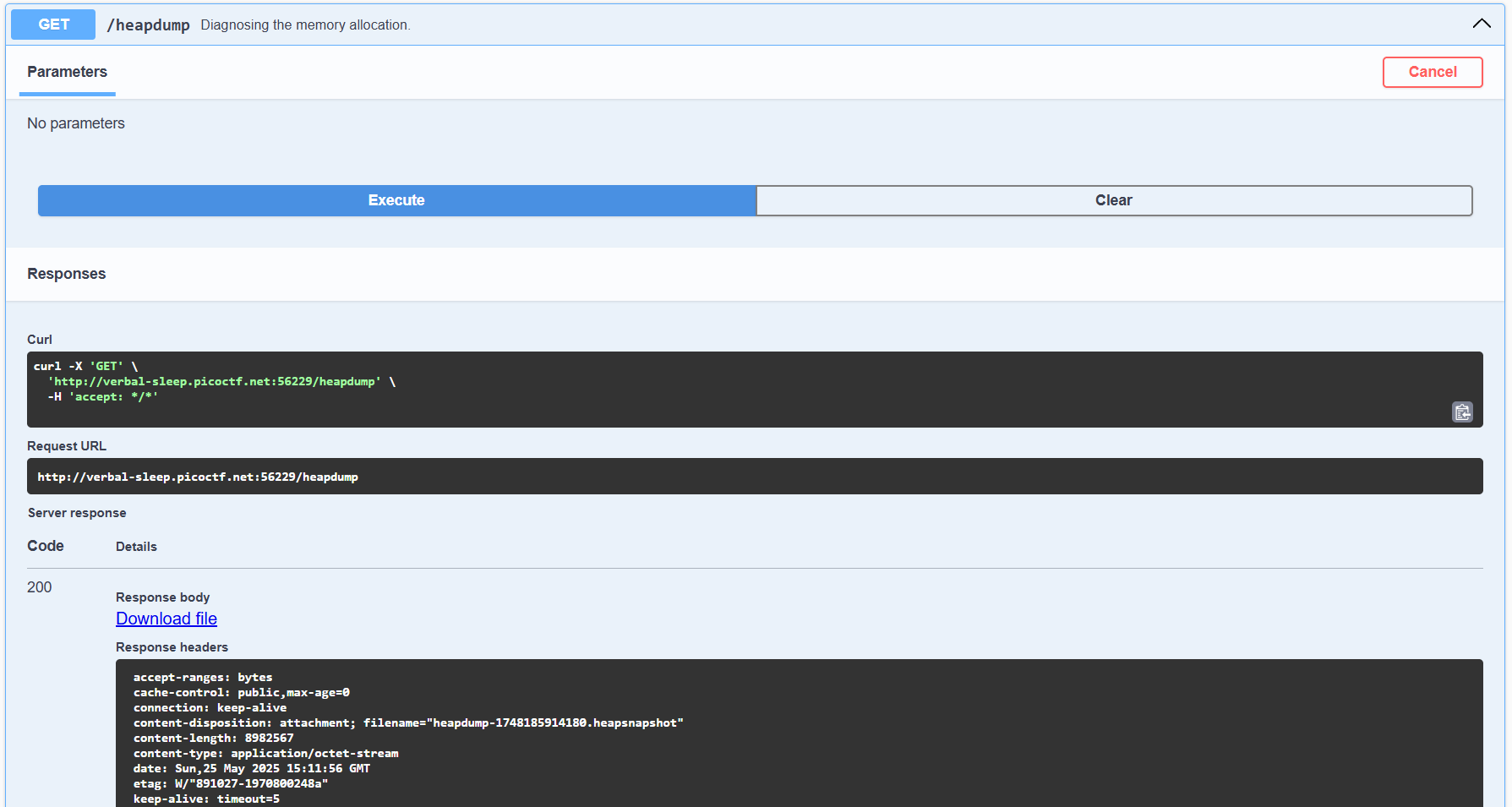
By analyzing the contents of this file and searching for the string picoCTF, the challenge flag can be uncovered.
> cat heapdump-1748185770090.heapsnapshot| grep "picoCTF"
picoCTF{Pat!3nt_15_Th3_K3y_388d10f7}
"picoCTF News API",
"Welcome to the picoCTF News API documentation! This documentation provides a detailed overview of the available API endpoints for managing and retrieving news posts.",
🚩Flag
picoCTF{Pat!3nt_15_Th3_K3y_388d10f7}