Ph4nt0m 1ntrud3r
- Description: A digital ghost has breached my defenses, and my sensitive data has been stolen! 😱💻 Your mission is to uncover how this phantom intruder infiltrated my system and retrieve the hidden flag. To solve this challenge, you'll need to analyze the provided PCAP file and track down the attack method. The attacker has cleverly concealed his moves in well timely manner. Dive into the network traffic, apply the right filters and show off your forensic prowess and unmask the digital intruder!
- Difficulty: Easy
🔎 Solution
Upon examining the pcap file, we observed that all packets use the TCP protocol and contain 3 distinct payload lengths: 4, 8, and 12 bytes.
Looking at the first packet, we found a base64-encoded string in the TCP payload: ezF0X3c0cw==. Decoding this yields {1t_w4s, which appears to be part of a flag.
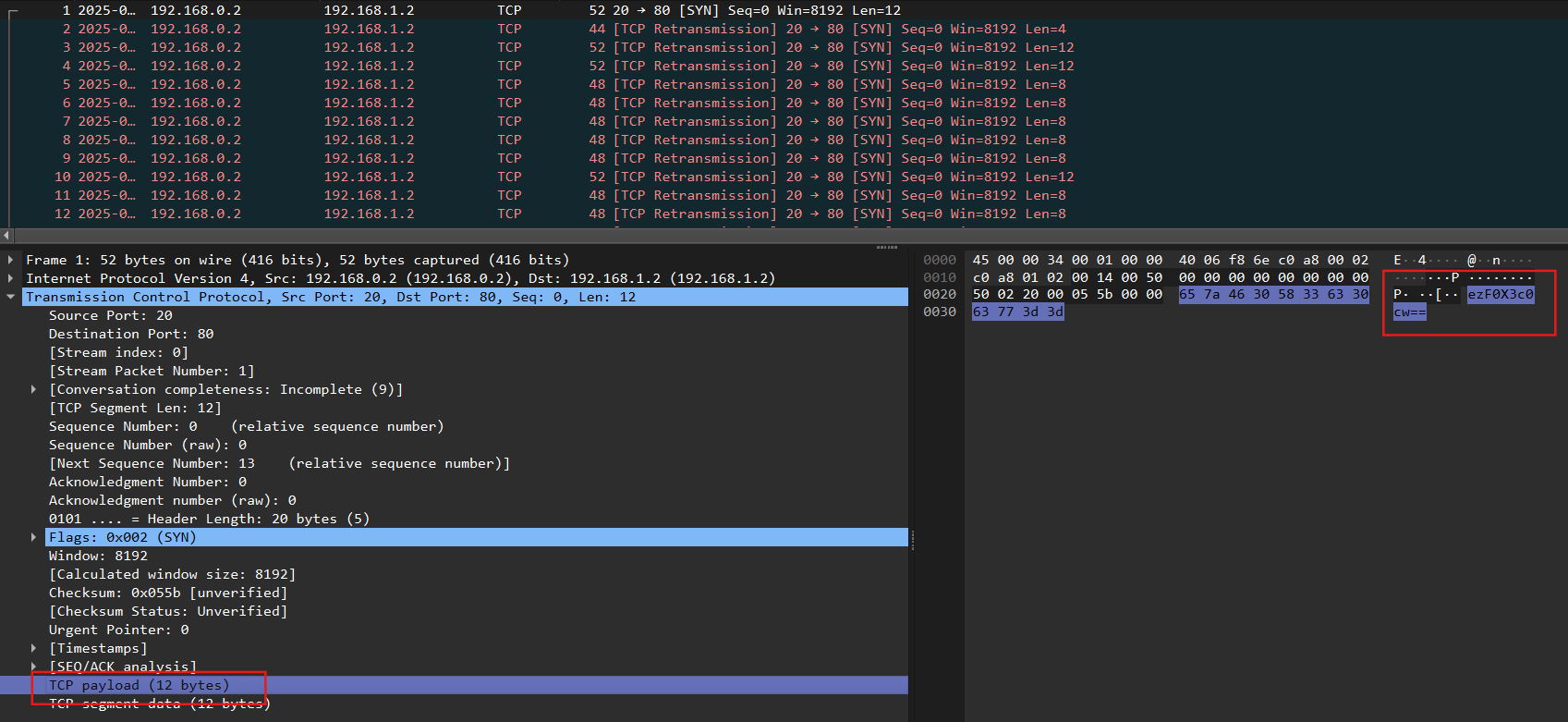
To extract the remaining parts, we wrote a Python script to parse the pcap file and retrieve the TCP payloads of all packets with a length of 4, 8 and 12 bytes. These payloads were then base64-decoded.
from scapy.all import rdpcap, TCP
import base64
packets = rdpcap("myNetworkTraffic.pcap")
decoded_payloads = []
valid_lengths = [4, 8, 12]
for pkt in packets:
if pkt.haslayer(TCP):
tcp_layer = pkt[TCP]
raw_payload = bytes(tcp_layer.payload)
if len(raw_payload) in valid_lengths:
try:
decoded = base64.b64decode(raw_payload).decode('utf-8')
decoded_payloads.append(decoded)
print(decoded)
except Exception as e:
print("")
After concatenating the decoded strings, we successfully reconstructed the complete flag.
> python script.py
{1t_w4s
}
4b57909
_34sy_t
nt_th4t
bh_4r_d
picoCTF
🚩Flag
picoCTF{1t_w4snt_th4t_34sy_tbh_4r_d4b57909}